Using Customer Service / Support
April 4th, 2016 Our support team often gets complimented that we have the best support in the industry, and that our customers tell their friends and colleagues about us all the time. One of our team has even once been “accused” of cloning himself because he’s always there.
Our support team often gets complimented that we have the best support in the industry, and that our customers tell their friends and colleagues about us all the time. One of our team has even once been “accused” of cloning himself because he’s always there.
As you can imagine, this is of course nice feedback to hear. Then this….
This morning I had a chat session with a customer that’s been with us for a few years, and he was looking for information on how to transfer the registration and hosting away to another provider. We have domains that transfer in to us and away from us.
Normally when we get a transfer away I inquire as to the reason for the transfer. The reason he gave was that he could not get the free basic hosting service to work. I asked if he’d contacted our support team for help, and his initial reply was yes. I wanted to check with whom he spoke, and turned out he had not contacted our support team, and that’s a shame.
He’s already got the transfer process underway, and of course we recommend our customers rights to move their domains to another registrar if they so choose. He’s moving to a registrar that does charge for Whois privacy, so will be paying quite a bit more for the registration service. Moving the domain’s registration and hosting will also not necessarily solve the issues he’s having with hosting.
So the take away from this is if you are having an issue with an R4L service, please get in touch with our support team. It’s not really possible for our team to know what customers are having issues with connecting to a mail account, server, or other issue unless we hear from you. Usually these kinds of issues are pretty quick for us to look into, and once resolved, you can get to using the hosting or mail service. In the case with this particular customer, not only could we have helped him months ago to get his site online, but he’d still be able to take advantage of the free hosting and Whois privacy we provide with the domain registration. Where he’s transferring doesn’t provide these free services, so his cost per year will be going up substantially.
Getting in Touch with the R4L Team
Secure Online Chat
Our newest way to get in touch with the support team is via the secure chat from our website. Simply go to https://Register4less.com and click on Chat Now – Online. The chat session between you and the agent that answers your chat is fully encrypted, so if you’re renewing a service with us, it’s safe to provide payment information over the chat. All chat sessions automatically will create a transcript in our support ticketing system.
Support Ticketing – Email
Our support address is support@Register4Less.com, or support@R4L.com. All email there gets tracked by a ticketing system. Tickets can be transferred between agents, be assigned a reminder date, etc.
Toll-Free Phone
You can also reach our team by calling within the US and Canada toll free 1 (877) 905 – 6500. Outside of North America, call int + 1 (514) 905-6500. If you are calling outside of our core office hours (9 – 5 Eastern), please leave a voice message and we will call you back as soon as we are able.


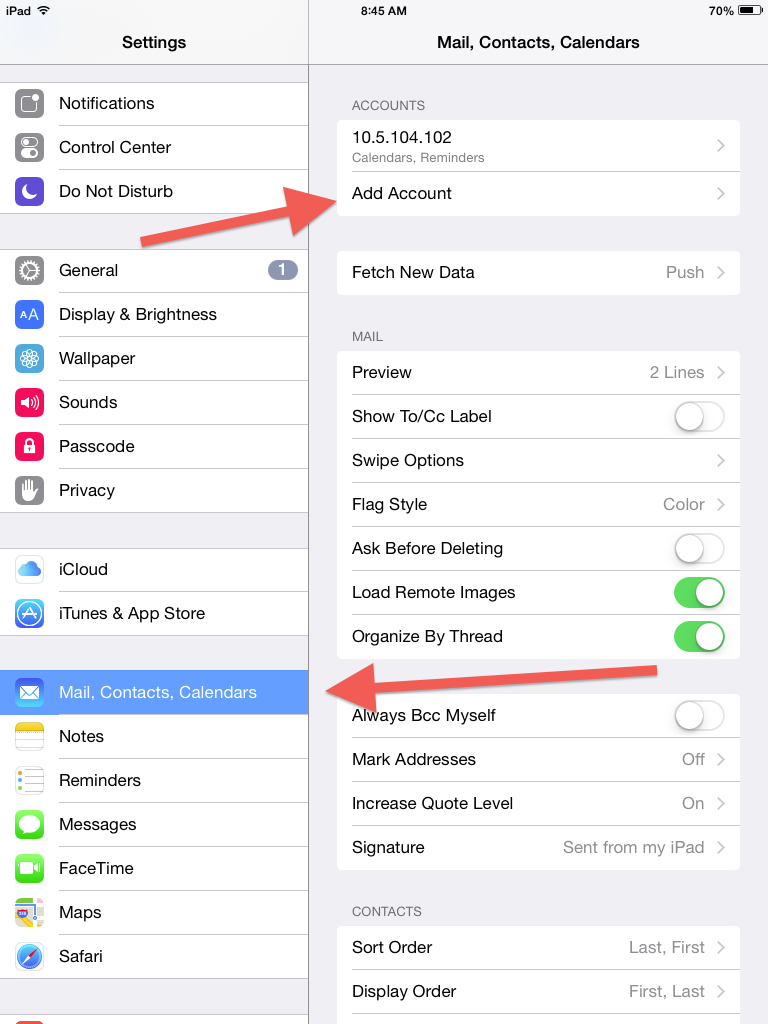

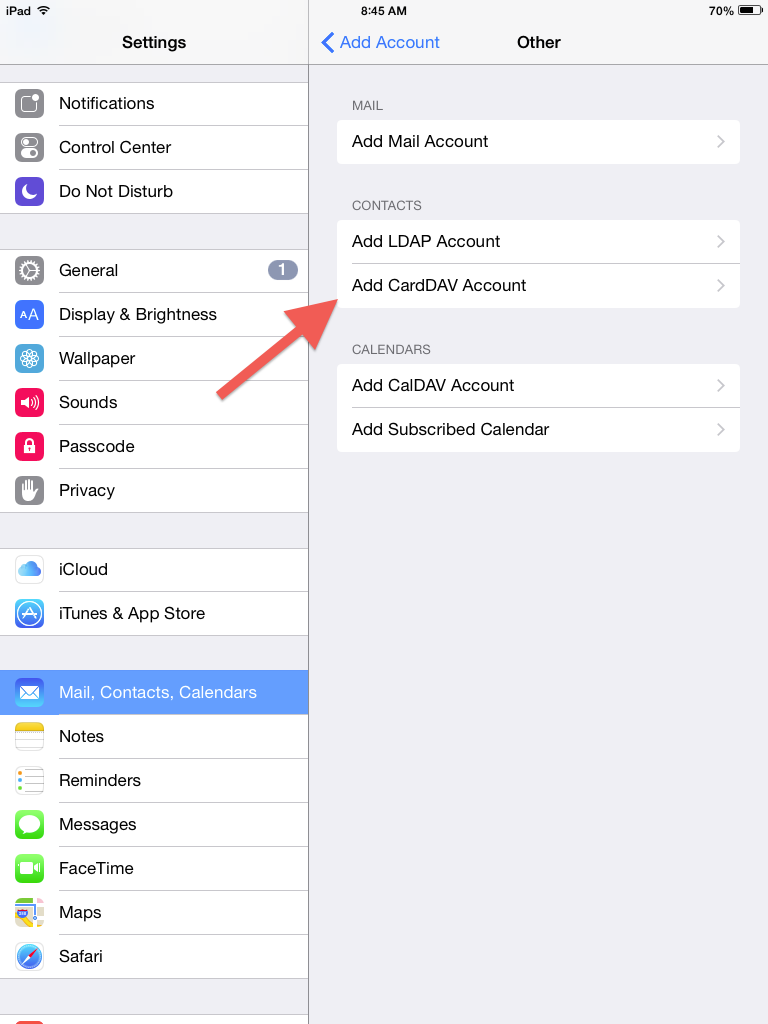
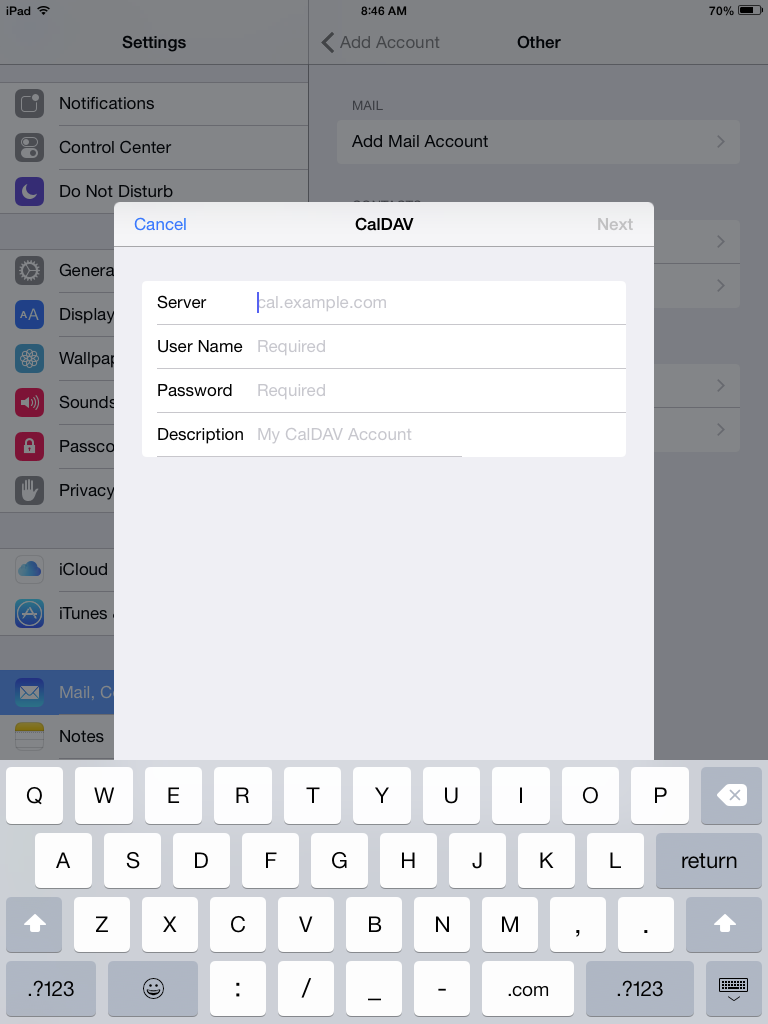
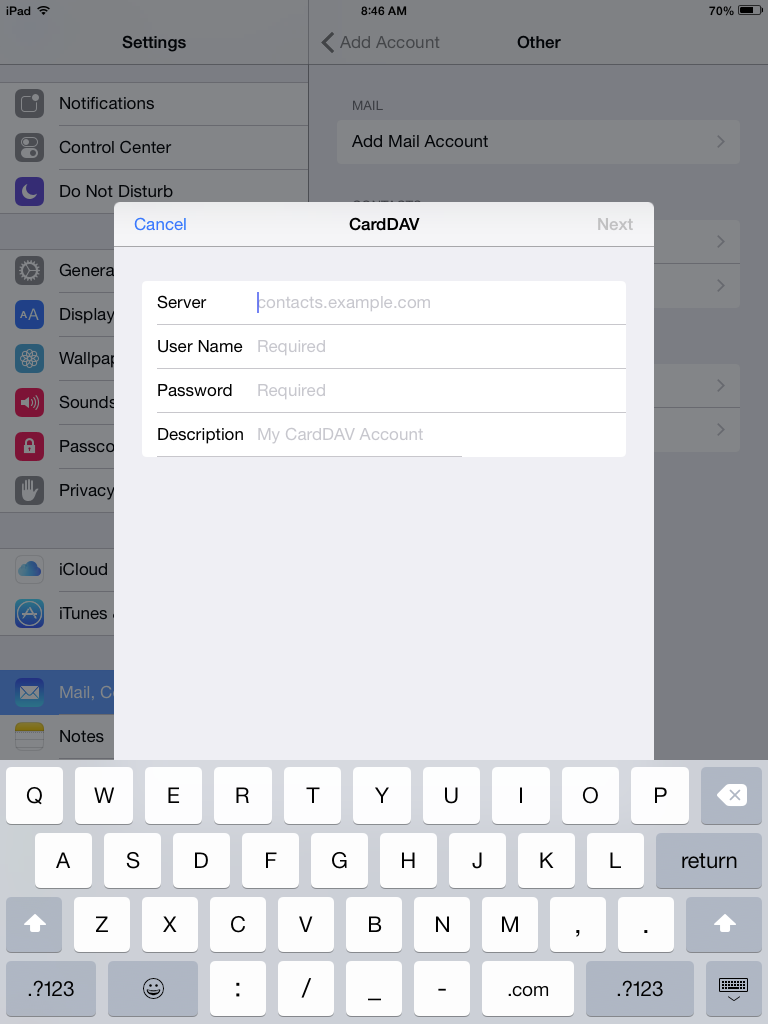
 Unified Logins
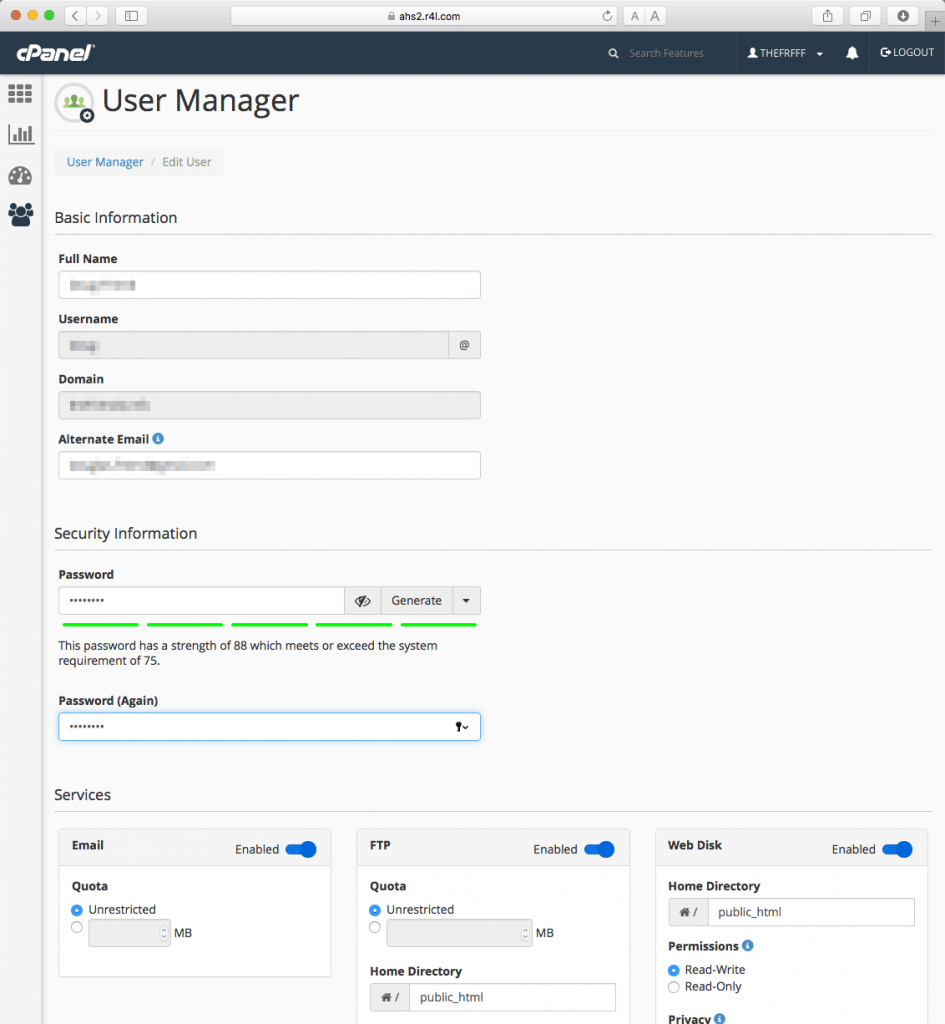
Unified Logins The User Manager
The User Manager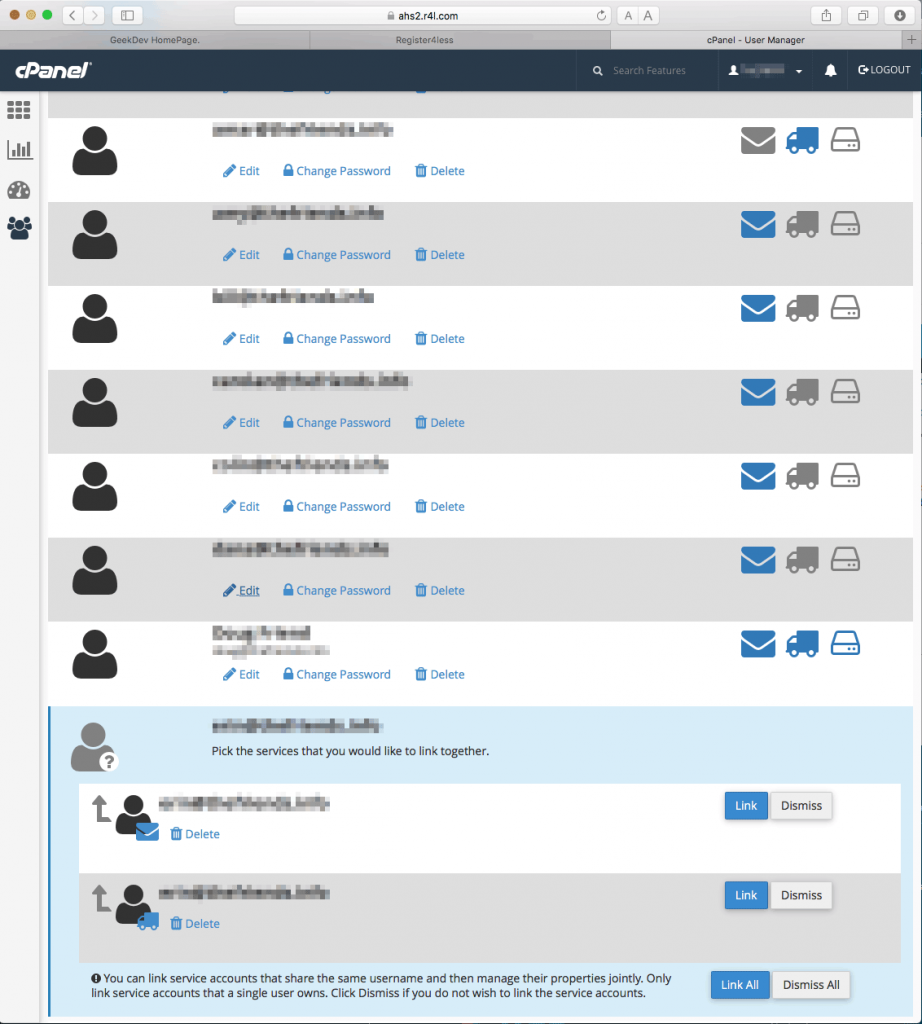
 A lot of sites will use a captcha with the form that needs to be entered in correctly in order for the comment to be accepted. While captchas certainly will help reduce spam, it puts the load on your visitor to fill this in correctly, and you risk annoying them or stopping them from submitting a valid comment.
A lot of sites will use a captcha with the form that needs to be entered in correctly in order for the comment to be accepted. While captchas certainly will help reduce spam, it puts the load on your visitor to fill this in correctly, and you risk annoying them or stopping them from submitting a valid comment. Usually, for the weekly blog post we try to write about something informative, about a new service we’re rolling out, etc. This past Wednesday, though, we had an interesting incident in our support team we’d like to share with you.
Usually, for the weekly blog post we try to write about something informative, about a new service we’re rolling out, etc. This past Wednesday, though, we had an interesting incident in our support team we’d like to share with you. Retail Advanced Hosting Plans
Retail Advanced Hosting Plans
 New Softaculous Default Settings
New Softaculous Default Settings With over 10.7 million downloads, WordFence is the most downloaded WordPress security plugin, and reputedly the best security plugin. WordFence will help you scan your site for malware/hacks, and help clean the site if problems are detected.
With over 10.7 million downloads, WordFence is the most downloaded WordPress security plugin, and reputedly the best security plugin. WordFence will help you scan your site for malware/hacks, and help clean the site if problems are detected. One of the Internet’s most valuable and very carefully guarded secret is the complex algorithm used by the search giant Google uses to rank pages on the Internet. Recently, though, Google announced
One of the Internet’s most valuable and very carefully guarded secret is the complex algorithm used by the search giant Google uses to rank pages on the Internet. Recently, though, Google announced